Cybercrime , Fraud Management & Cybercrime , Ransomware
After Conti Ransomware Brand Retires, Spinoffs Carry On
Attacks Tied to Apparent Spinoffs or Subsidiaries Black Basta and Hive Have Surged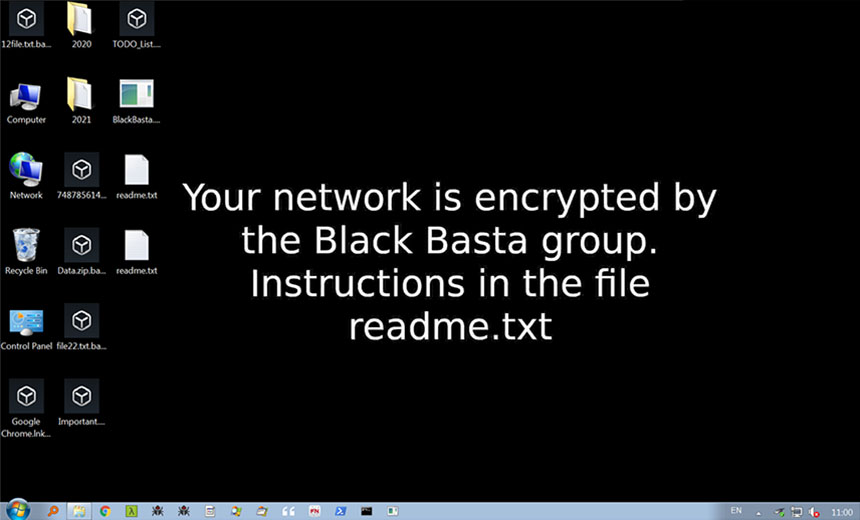
The Conti ransomware group supposedly pulled the plug on its operation on May 19. Security experts say the group's activities appear to have continued, albeit in the form of numerous spinoffs, startups or loosely connected operations.
See Also: Ransomware Response Essential: Fixing Initial Access Vector
Fallout from the notorious ransomware group's public support of Moscow in its war against Ukraine is at least partially responsible for the shift, researchers say.
Conti's threat to target the critical infrastructure of any country launching cyberattacks against Russia and other "publicity stunts" backfired by definitively connecting the group to the Russian government, Vitali Kremez of Advanced Intelligence tells Information Security Media Group.
"What's happened in the real world: Lots of crypto traders, insurance providers, and some of the companies stopped cooperating with them … literally stopped paying them," says the chief executive and chair of New York-based threat intelligence firm AdvIntel. Victims are increasingly worried that paying out puts them on the wrong side of U.S. sanctions that impose civil penalties even for unknowing violations.
"It affected their operations. It took away their major incentives to do cybercrime," he says of Conti. "They couldn't get money from their victims, and they couldn't understand why, for quite some time."
Conti's apparent response was to intensify a move to establish a number of other brands. AdvIntel says these may include Black Basta, Black Byte and Karakurt as stand-alone groups; Alphv/BlackCat, AvosLocker and HelloKitty/FiveHands as semi-autonomous groups, as well as multiple affiliates, not all of which appear to be focused on crypto-locking malware.
Research from AdvIntel indicates that Conti continued to launch high-profile attacks - for example, against the government of Costa Rica - designed to make the ransomware operation look as if it remained a going concern while also appearing to be distinct from the new efforts. Whatever the impetus for that attack, the damage to Costa Rica was very real, and the government declared a state of emergency as a result (see: Conti Ransomware Group Retires Name After Creating Spinoffs).
Leaks Highlight Ties to Russia
Further blowback over Conti's public backing of the Kremlin came in the form of a Ukrainian security researcher taking revenge by leaking extensive information tied to the criminal operation, including addresses for cryptocurrency wallet addresses containing bitcoins worth $1.4 billion as of Friday's exchange rates.
"The published data included private chat logs, the servers they use, a list of victims and details of bitcoin wallets, which stored over 65,000 BTC in total," cybersecurity firm Group-IB says in a report. "The leaked chats revealed that the group had faced serious financial difficulties and that their boss had gone off the radar. Yet its members were fully prepared to restart the project."
The leak of Conti's internal communications revealed a well-run business operation staffed by about 200 employees, including an HR department, groups of specialists in various types of cybercrime and open-source intelligence, as well as advanced research and development to find innovative new ways to extort victims.
The group's public embrace of the Kremlin and the leaks confirmed what many security experts had long suspected: Conti was based in Russia, staffed by Russian speakers and closely obeyed the Russian cybercrime rule of never hitting domestic targets (see: Russia's Cybercrime Rule Reminder: Never Hack Russians).
"The geography of Conti's attacks is vast but does not include Russia," Group-IB says. "The group clearly adheres to the unspoken rule among Russian-speaking cybercriminals: Do not attack Russian companies. Most attacks occur in the United States (58%), followed by Canada (7%), the United Kingdom (7%), Germany (6%), France (4%) and Italy (3%)."
Based on the leaked communications, Conti's leader, known as "Stern," apparently had close ties to Russia's Federal Security Service, known as the FSB.
Serious Ransomware Concern
Conti had ranked as one of the most damaging ransomware operations in recent years, especially following the demise of REvil/Sodinokibi in the summer of 2021.
Remaining extremely active until its apparent demise, Conti attacks ranked second only to LockBit 2.0 in terms of known victims for the month of May. But multiple groups apparently tied to the organization formerly known as Conti appeared to be already well established at that point.
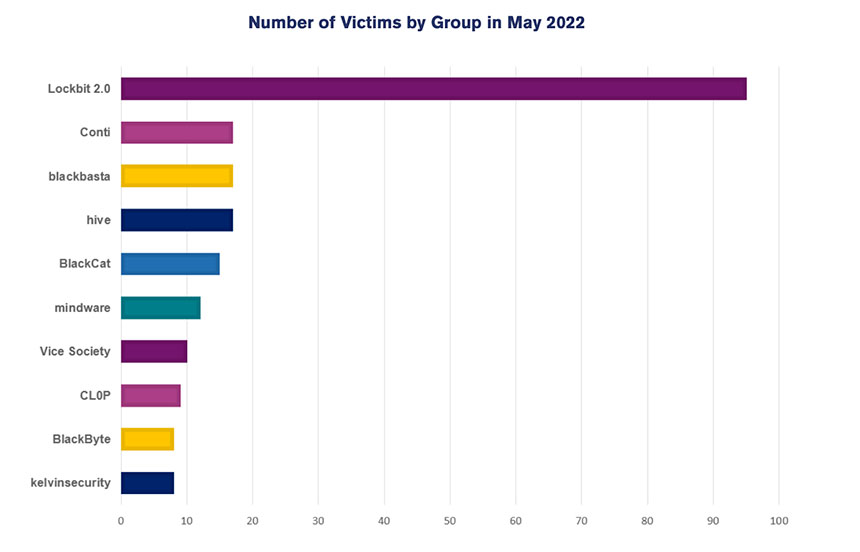
Kremez says a particular area for exploration by Conti spinoffs appears to be exfiltrating data without leaving systems encrypted and then extorting victims with a threat to release the stolen data. This strategy could help the group evade some scrutiny by law enforcement officials and is also quicker and easier to execute, he says (see: Conti Ransomware Group Explores Post-Encryption Future).
Black Basta and Hive Attacks Surge
If operations being carried out in the name of Conti have ceased, the same isn't true for its apparent spinoffs. Notably, Hive hit another Costa Rican government target at the end of May, following on Conti's April attack.
"Hive may be working with Conti to support the group with a rebrand and to evade international sanctions concerning extortion payouts to cybercriminals operating in Russia," consultancy NCC Group reports.
Black Basta, which only launched in April, has already publicly claimed 36 victims and has been partnering with the QBot malware operation to spread its crypto-locking ransomware, reports Lior Rochberger, a senior threat researcher at threat intelligence firm Cybereason.
"Not much is known about the new Black Basta gang, as they have not begun marketing their operation or recruiting affiliates on hacking forums," Rochberger says in a blog post. "However, due to their ability to quickly amass new victims, different researchers believe that it's not their first time" playing the ransomware game.
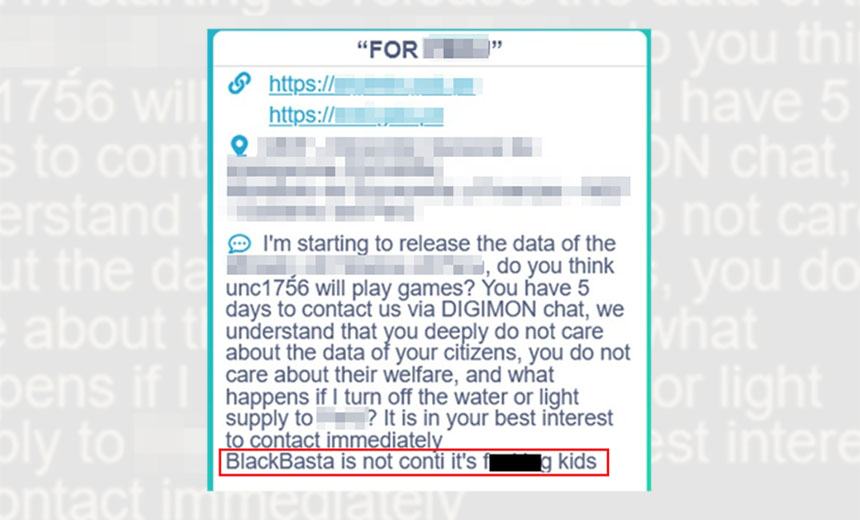
Conti, meanwhile, denies having anything to do with Black Basta. But this is hardly definitive; ransomware-wielding attackers, like any type of criminal, regularly lie, especially when they have a financial incentive to do so (see: Secrets and Lies: The Games Ransomware Attackers Play).













