Fraud Management & Cybercrime , Social Media
Cybercrime Forum Dumps Stolen Details on 5.4M Twitter Users
But Information Compiled by Other Attackers May Involve Millions of Other Accounts
Information amassed on 5.4 million Twitter users by an attacker who abused a social network API is available online for free. Twitter has previously confirmed that breach and theft of information, but a researcher suggests that at least one additional attacker also abused the feature to steal account details pertaining to millions of other users.
A description of the dumped database says it includes the 5.4 million users' usernames, display names, bios, locations, email addresses and phone numbers. The attacker amassed the data by exploiting APIs tied to the "let others find you by your phone" feature.
According to an analysis conducted by the Breached forum, which is hosting the stolen data, 681,184 of the email addresses, comprising 12% of dumped email addresses, don't appear to have been previously leaked.
Twitter confirmed the breach in August, saying it had learned about the flaw in January via its bug bounty program and immediately fixed it (see: Twitter Confirms Zero-Day Bug That Exposed 5.4M Accounts).
Twitter said the flaw meant that "if someone submitted an email address or phone number to Twitter's systems, Twitter's systems would tell the person what Twitter account the submitted email addresses or phone number was associated with, if any."
It said that the feature had been added in June 2021 and that when it learned how the functionality could be abused in January via the bug bounty report, "we had no evidence to suggest someone had taken advantage of the vulnerability."
But in July, Twitter said it had learned via a press report that an attacker had used the flaw in December 2021 to compile information on users and confirmed that the stolen data was legitimate. Twitter said it was directly notifying all affected users that it could identify and was also issuing a public alert "because we aren't able to confirm every account that was potentially impacted, and are particularly mindful of people with pseudonymous accounts who can be targeted by state or other actors."
Now, security researcher Chad Loder is warning that much more information appears to have been stolen by unknown attackers who also abused the feature.
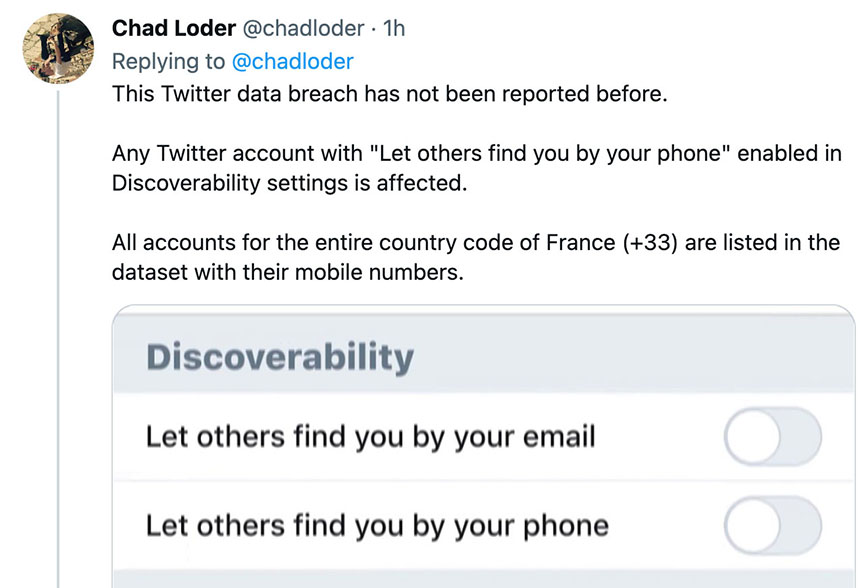
"I have just received evidence of a massive Twitter data breach affecting millions of Twitter accounts in EU and U.S.," he reported Wednesday in a series of tweets. "I have contacted a sample of the affected accounts and they confirmed that the breached data is accurate."
Loder adds that "the dataset includes verified accounts, celebrities, prominent politicians and government agencies."
Loder's account was subsequently suspended by Twitter.
He has taken his warnings and analysis to rival service Mastodon.
Bleeping Computer reports that it has confirmed that multiple pieces of information contained in the data set obtained by Loder are legitimate and that the database might include information on 17 million accounts. It adds that Breached forum owner Pompompurin claims to not be responsible for compiling the larger database.
It's not clear how many other criminals or nation-states may have abused the Twitter feature to obtain information on accounts, as well as to potentially unmask owners of pseudonymous accounts.
Twitter, which reportedly no longer employs dedicated communications staff, did not respond to a request for comment.













