COVID-19 , Cybercrime , Fraud Management & Cybercrime
Cybercrime Review: Hackers Cash in on COVID-19
Phishing, Spam, Malware, Social Engineering and Other Recent Attack Trends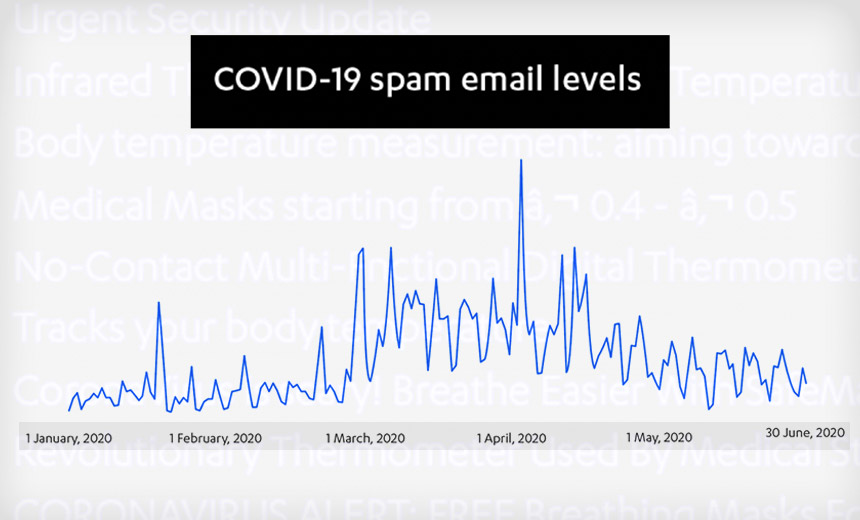
After reviewing online attack trends for the first half of the year, numerous cybersecurity firms agree: COVID-19 was king. As the pandemic has reshaped how many live and work, so too has it driven attackers to attempt to exploit work-at-home challenges and virus fears.
But that’s only part of the attack landscape picture involving broader phishing, social engineering, malware, business email compromise and other attack, fraud and scam trends that security firms have traced for the first six months of this year - as described in newly released reports.
Each security firm's analysis of the trends differs because each is based on attacks seen by the organization's customers as well as honeypots and investigations.
With that caveat, here's a sampling of the findings.
Phishing Attacks Rise and Fall
Phishing attacks surged after lockdowns began in February and March. "Fortunately, the sudden flood of COVID-themed email attacks began to subside in May," Finnish security firm F-Secure reports in its Attack Landscape H1 2020 study. "Like the pandemic, the problem hasn’t gone away, but it seems to have improved."
Other security firms have traced a similar rise and fall in phishing attempts.
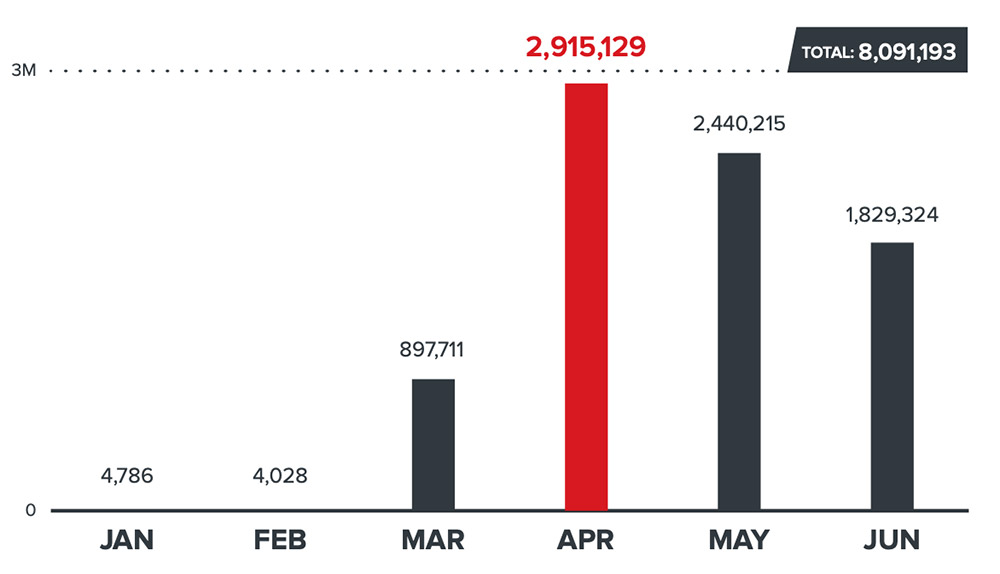
As the pandemic continued, more malicious emails featured COVID-19 themes and contained "a mixture of spam, phishing attempts and malicious attachments as cybercriminals capitalized on the fear and uncertainty generated by the crisis," F-Secure says.
The firm says the most common subject line for a malicious email without an attachment was "Urgent Security Update" and, of the COVID-19-themed malicious emails with attachments, 75% of the attachments were either Lokibot or Formbook.
Tokyo-based Trend Micro notes that "93.5% of the email threats we detected contained both a malicious file attachment and a malicious link."
Many of these emails led to phishing sites, it says.
Social Engineering Surges
Before the pandemic began, social engineering attacks had been on the decline, according to a review of breach trends for the second quarter of this year published by London-based Beazley, the parent company of specialist insurance businesses - including six Lloyd's syndicates - with operations in Europe, the U.S. and Asia.
But after the COVID-19 outbreak began, social engineering attacks - including phishing and attackers perpetrating fraudulent instruction schemes - began to rise.
"The arrival of the global pandemic provided cybercriminals with the perfect cover for ramping up email attacks," Beazley says. "Coinciding with the increase in remote working during the second quarter, our global data has shown employees have been more likely to fall for social engineering scams, with organizations in the middle market most likely to be victimized."
Such scams often involve tricking someone into changing wire instructions or moving funds to an attacker-controlled account, it says.
Sometimes, however, scammers remotely hack into systems. For example, one scam recently seen by Beazley, which hit a university, involved attackers ascertaining which vendors were enrolled in the institution's automated clearing house system for regular payments. For more than six weeks, just before regular payments were set to be transferred, attackers accessed the ACH system, changed the legitimate vendor's bank account to an attacker-controlled one, waited for the funds to be received and then changed the bank account details back.
"Almost $600,000 of payments were diverted before the receiving bank identified the suspicious activity and shut it down," Beazley says.
BEC Scams Continue
Trend Micro notes that the volume of business email compromise scams has increased in recent months.
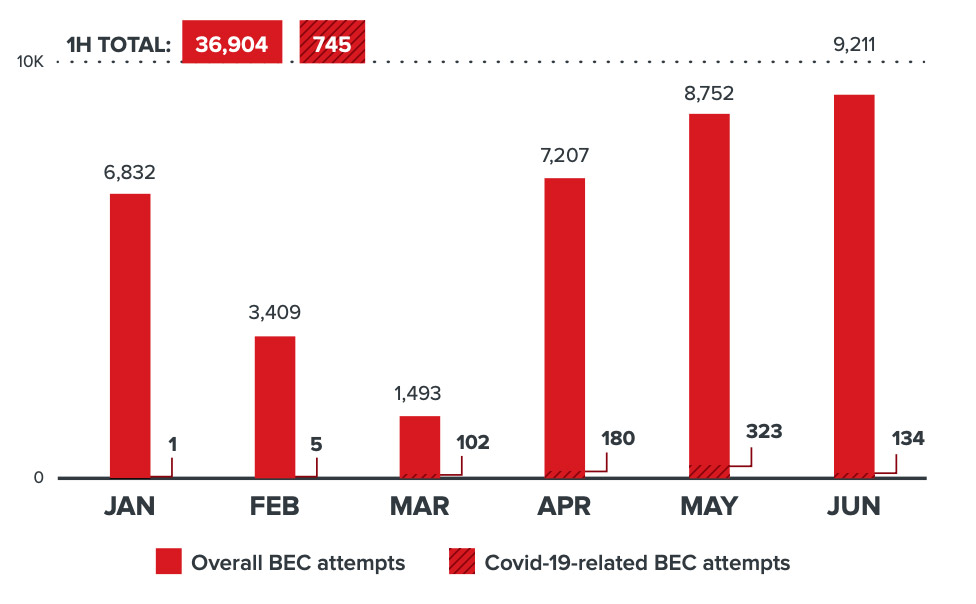
"Scammers also used business email compromise schemes using COVID-19-related topics as a hook," it says. Regardless of whether attackers used a COVID-19 lure, "the effectiveness of these scams was likely bolstered by the fact that new remote work arrangements made it more difficult to keep track of communication between members of an organization."
Spyware and Information Stealers Proliferate
Which strains of malware have been especially hot this year? Singapore-based Group-IB says its Computer Emergency Response Team, CERT-GIB, found that, for the first half of the year, 43% of malicious emails had spyware attached or included links for downloading spyware or information stealers, 17% contained downloaders for installing malware onto systems, 16% led to backdoors and 15% involved banking Trojans.
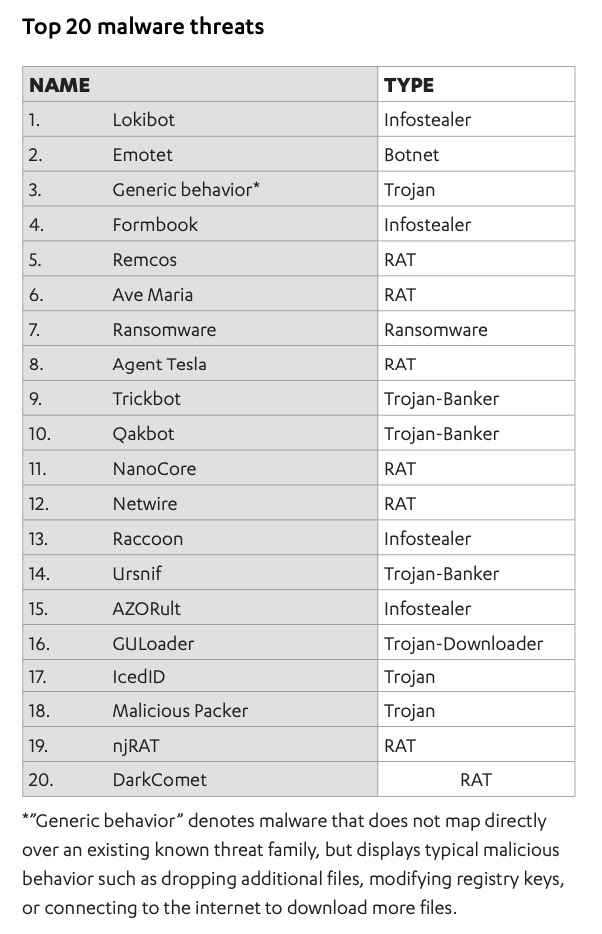
Opportunistic ransomware attacks, however, have declined from involving about half of all malicious email attacks in the second half of 2019 to less than 1% of all such attacks in the first half of this year.
Security firms offer widely varying accounts of what was the most-seen malware in the first half of the year.
Group-IB says the malware it most commonly saw was Trojan RTM (accounting for 30% of all malware), followed by LOKI PWS spyware (24%), the Formbook information stealer (12%), the remote access tool Agent Tesla (10%), the Nanocore information stealer (7%) and Hawkeye credential-stealing malware (5%).
F-Secure reports that the most popular method for spreading malware in the first half of the year was email. That was followed by malware being manually installed - both by attackers and users - in 35% of cases, up from 24% last year.
"This rise could be due, in part, to cybercriminals registering thousands of fake 'Zoom' domains to trick users into downloading malware disguised as the videoconferencing software," F-Secure says. "Another attacker tactic is to manually install ransomware as a second-stage payload after having gained an initial foothold into the company through an unsecured RDP port."
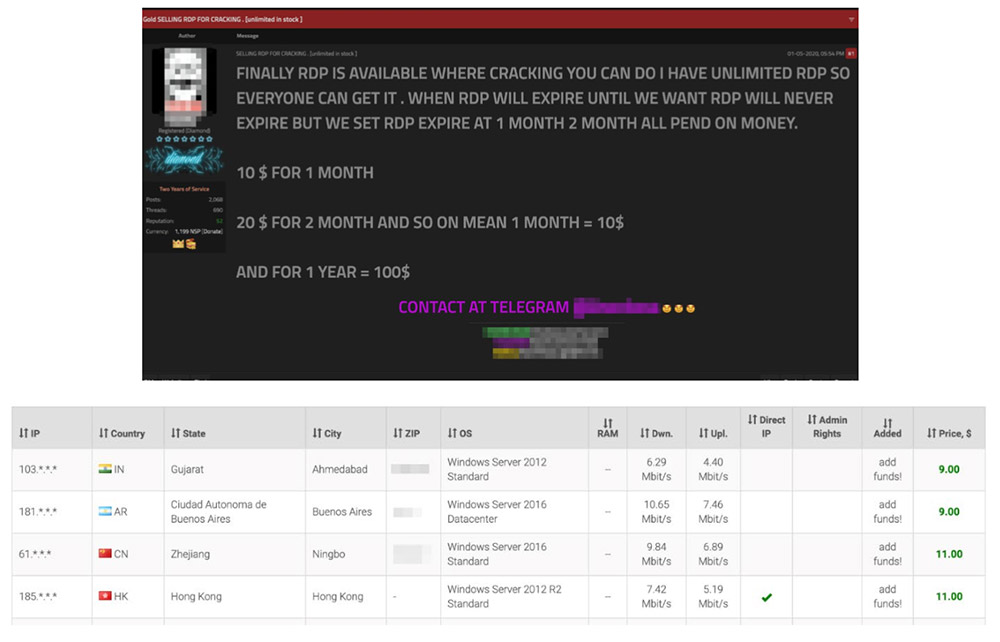
Accessing poorly secured remote desktop protocol connections remains a common way for attackers - including ransomware-wielding gangs - to remotely access victims' networks, researchers warn.
Criminal Paydays Continue
In its Threat Hunting Report for the first half of the year, Sunnyvale, California-based CrowdStrike says that, of the attacks it could attribute, 82% were tied to criminals and 18% to nation-state attackers. State-sponsored attacks have remained constant for some time, while the overall level of online crime has increased, the company says.
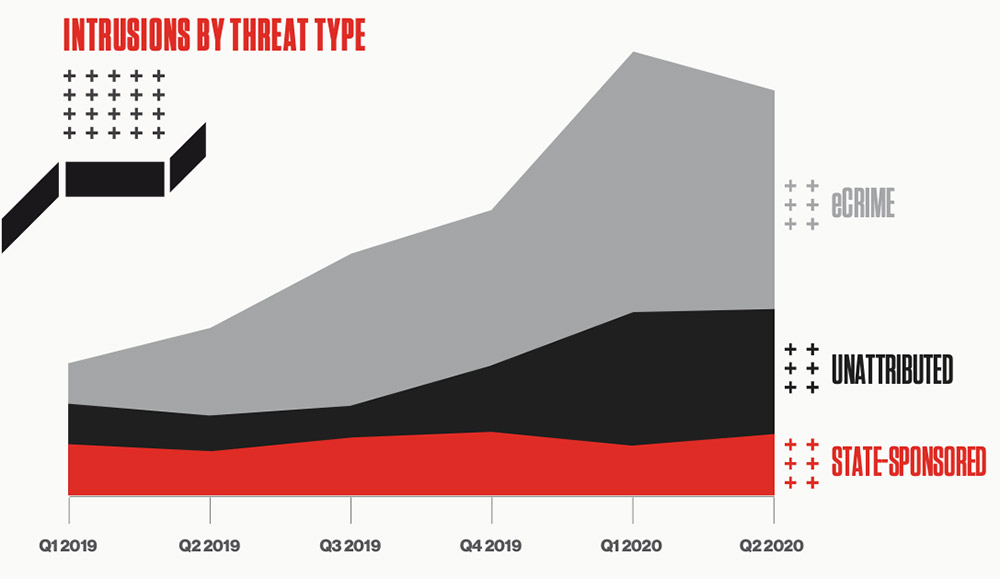
One reason online crime is such a draw, CrowdStrike says, is the potential for gangs to achieve larger payoffs via big-game hunting, which refers to taking down big targets in an effort to gain massive ransom payoffs. Another trend, CrowdStrike says, is the growth in ransomware-as-a-service offerings, which offer unskilled attackers extremely sophisticated and effective crypto-locking malware tools.
Focus on Best Practices
While attackers' tools and tactics continue to evolve, security experts say the basic best practices that an organization should pursue to protect itself largely remain constant.
F-Secure advises: "Stay on top of updates and patches, lock down services that are outright vulnerable or could lead to further compromise, try to segregate employees’ work computing environments from their personal, always remain vigilant for spam or phishing campaigns and educate employees about these campaigns."













