Fraud Management & Cybercrime , Ransomware
REvil and Conti Ransomware Spinoffs Refine Attack Strategies
'Callback Phishing' Increasingly Used to Trick Victims Into Granting Remote Access
Ransomware groups come and go, but the individuals behind them persist in bringing their hacking and extortion skills to bear as part of fresh operations.
See Also: OnDemand | Hacker’s Guide to Ransomware Mitigation and Recovery
Take the aftermath of what were two of the world's most formidable ransomware gangs: REvil and Conti.
REvil - aka Sodinokibi - disappeared in July 2021 after being targeted by multiple law enforcement agencies, briefly spluttered back to life next September and then seemed to be gone for good.
Since then, researchers have spotted at least three apparent REvil spinoffs:
- Ransom Cartel: It was first spotted in December 2021, using malware apparently based on REvil's source code, which experts don't think the group has shared with outsiders.
- BlogXX: It appears to date from April, when multiple security researchers told Bleeping Computer that a sample of the malware appeared to have been compiled from REvil source code. The researchers said the ransomware may be run by a REvil core developer. The group's ransom note also claims it's called Sodinokibi.
- Spectre: First seen in April, "it's another gang that has a ransomware that either was coded to fake REvil or they are also using REvil's ransomware - modified/hex-edited sample or they have REvil's source code," researchers at MalwareHunterTeam reported.
The operators of Conti, meanwhile, retired the brand name in the spring after making a disastrous business decision: They publicly backed Russian President Vladimir Putin's decision to invade Ukraine, leading to a massive falloff in ransom payments to the group. But before retiring the brand, Conti spun off multiple smaller operations using different names (see: Ransomware Ecosystem: Big-Name Brands Becoming a Liability).
Apparent Conti spinoffs include Alphv/BlackCat, AvosLocker, Black Basta, HelloKitty, Quantum, Roy/Zeon and Silent Ransom.
Conti Spinoffs Use BazarCall Tactics
This year, ransomware groups have faced a growing problem: Fewer victims are paying a ransom (see: Ransomware Payments: Just 46% of Victims Now Pay a Ransom).
It's no surprise that Conti spinoffs have been honing a set of strategies aimed at restoring profit margins. "Through September, it became clear that groups like Quantum, Royal, SilentRansom and other BazarCall collectives became especially dangerous, with a spike in successful attacks," says Yelisey Boguslavskiy, head of research at New York-based threat intelligence firm Advanced Intelligence - aka AdvIntel - in a new report.
In particular, the groups have been adopting and refining BazarCall - previously known as BazaCall - tactics. This is a "callback phishing" methodology that involves attackers telephoning victims, impersonating the technical staff at a software vendor they use, and trying to trick them into giving attackers the ability to install remote-control software on the victim's PC. If successful, attackers use this to install malware and attempt to further penetrate the network.
This practice was pioneered by the Ryuk group in early 2021, before being relaunched in March by Conti, as AdvIntel reported.
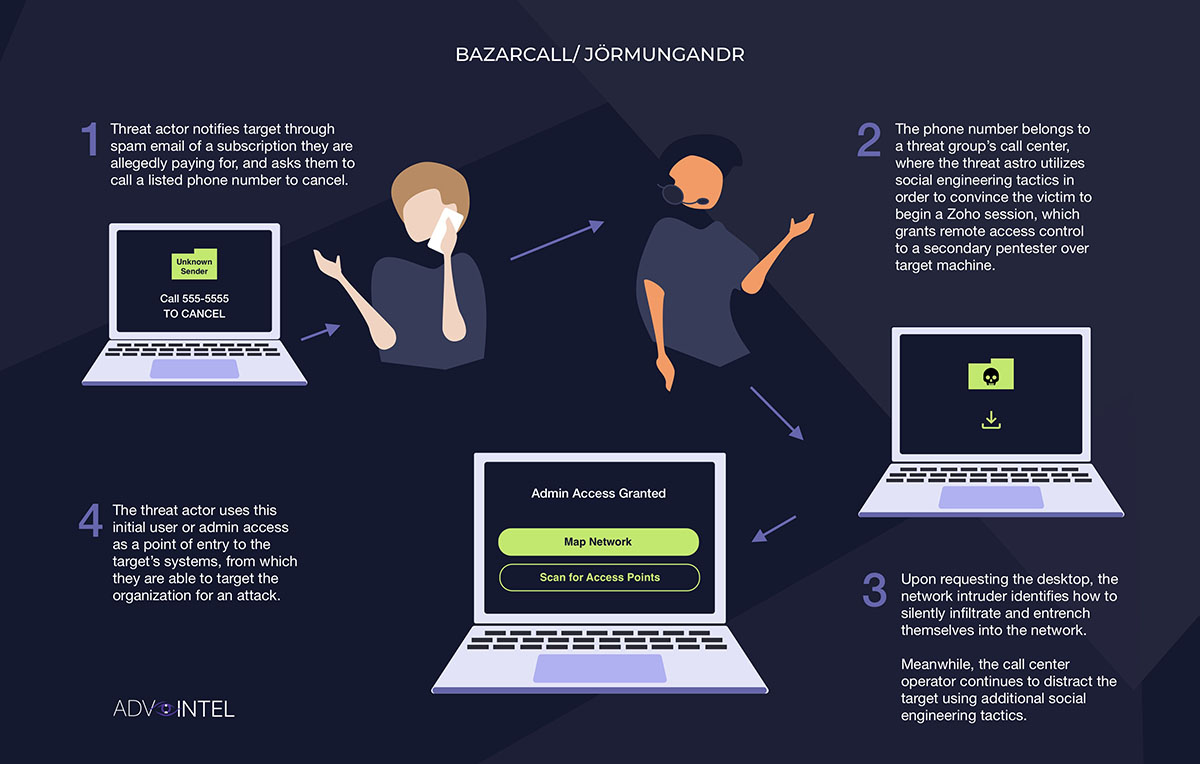
AdvIntel's Boguslavskiy says this is the timeline of how three Conti spinoffs have been using callback phishing:
- BazarCall: The callback phishing group split from Conti in April, launching as a new group called Silent Ransom.
- Quantum: This Conti Team Two spinoff in June began to callback phishing tactics that it calls Jörmungandr - the name of a sea serpent in Norse mythology.
- Roy/Zeon: Also launched in June, this group spun off from Conti Team One - which had created Ryuk - and began using callback phishing.
Callback phishing was developed to enable ransomware operations to hit preselected targets in a cost-effective manner, which they previously were unable to do.
"Traditionally, ransomware has been reactive. Targets are random, decided by which ones happen to fall prey to infection," Boguslavskiy reports.
But this "spray and pray" approach typically results in a low rate of infections. "Hypothetically, a ransomware collective could send out 1,000 Emotet infections that are able to yield access for just 10 organizations," he says. "The collective cannot afford to pick and choose in regards to their victims' revenues, jurisdiction, industry, etc. This cost/benefit ratio was severely limiting the potential of successful ransomware deployment, and therefore potential profit."
Of the groups using callback phishing tactics, Quantum so far appears to be the most successful, due to it taking a more holistic approach by not just focusing on callback phishing, but also refining its malware, building alliances with the IcedID and Emotet botnets to outsource their ability to gain access to endpoints, as well as continuing to use spam to disseminate its malware.
Given the apparent success of these callback phishing tactics, how long until other ransomware operations follow suit?













