Breach Notification , Card Not Present Fraud , Forensics
Sabre Warns Hotels: Card Data Potentially Compromised
36,000 Locations Use Breached Travel Giant's SaaS System
Travel industry software giant Sabre has alerted hotels that a hacker apparently breached its software-as-a-service reservation system and may have stolen payment card data and customers' personal details.
See Also: Quantifying The Total Cost of E-Commerce Fraud
More than 36,000 properties could have been affected by the breach of Sabre's SynXis Central Reservations system.
Sabre, based in Southlake, Texas, provides technology used by the global travel industry, including hundreds of airlines and thousands of hotel properties, and also operates a travel marketplace that processes more than $120 billion of global travel spending each year across 160 countries.
Sabre says the breach involved its SynXis Enterprise Platform. According to the company's website, that SaaS software is used at more than 36,000 locations, ranging from small, independent hotels to large, global chains, and provides both property management as well as a central reservations system.
"We are investigating an incident involving unauthorized access to payment information contained in a subset of hotel reservations processed through the Sabre Hospitality Solutions SynXis Central Reservation system," Sabre says in a May 2 10-Q quarterly filing to the U.S. Securities and Exchange Commission. That SaaS system is designed to provide rate and inventory management capabilities for hotels.
Sabre spokesman Timothy Enstice tells Information Security Media Group that it has hired FireEye's Mandiant to assist with its digital forensic investigation.
"Our Sabre Hospitality Solutions customers are being notified of the investigation with a commitment to keep them informed," Enstice says. "Consistent with our steadfast commitment to providing world-class security for our solutions and support for our customers, we have dedicated internal staff and independent cyber experts to complete this investigation as quickly as possible."
Enstice declined to comment on when the breach appears to have started, how long it persisted, how many locations were affected, how many payment cards may have been compromised or whether card issuers have seen signs of related card fraud. "Until the forensic investigation by our independent experts is complete and we have made any necessary notification to our customers, it is premature to speculate on other details," he says.
Payment Card Data Potentially Compromised
Enstice says Sabre's breach has been contained and the company is working with law enforcement agencies to investigate. "The unauthorized access has been shut off and there is no evidence of continued unauthorized activity," he says. "There is no reason to believe that any other Sabre systems beyond SynXis Central Reservations have been affected."

According to Sabre's SEC filing: "There is a risk that this investigation may reveal that PII, PCI, or other information may have been compromised."
Those are references to PII - personally identifiable information - as well as to data security regulations from the Payment Card Industry, which regulates how card data gets processed, stored or transmitted (see How Will PCI-DSS Evolve in Next 10 Years?).
Under California state law, meanwhile, PII can include an individual's first and last name, street address, email addresses, telephone number and Social Security number, or any other information that might be collected and used to identify that individual.
Sabre says that it does not yet know how much its breach investigation might cost - or what types of lawsuits might be filed against it as a result - but notes that it does have cyber insurance. "We maintain insurance that covers certain aspects of cyber risks, and we are working with our insurance carriers in this matter," its filing reads.
Sabre began directly alerting affected properties May 2 via a short statement, security blogger Brian Krebs first reported.
Hospitality Sector Under Fire
Sabre's potential payment card and PII breach warning to hotels is just the latest in a long line of hospitality sector breach reports, the vast majority of which trace to malware installed on point-of-sale terminals and the controllers and servers used to manage them.
Last month, for example, Intercontinental Hotels Group warned customers that malware had infected POS devices at 1,200 of its locations - including Crowne Plaza, Intercontinental, Kimpton and Holiday Inn properties - beginning in September 2016.
Other hotels experiencing similar breaches have included HEI Hotels & Resorts - which manages some hotels owned by IHG - as well as Hilton, Hyatt, Omni Hotels & Resorts, Starwood Hotels and Resorts and Trump Hotels, among others.
Third-party POS vendors are also under attack. In August 2016, Oracle warned that an attacker planted malware in a support portal for servicing and maintaining its MICROS POS systems - one of the mostly widely used POS systems in the world, with 330,000 customers in 180 countries.
Other, smaller POS vendors have also been targeted, including Cin7, ECRS, NavyZebra, PAR Technology and Uniwell. Those attacks were discovered by Alex Holden, CISO for Hold Security, which tracks the underground trade in stolen data.
Poor Preparation, Detection, Response
The POS breach epidemic in the hospitality sector - comprising both hotels and restaurants - is compounded by too many organizations' poor preparation, detection and response capabilities, according to Verizon's recently released 2017 Data Breach Investigations Report.
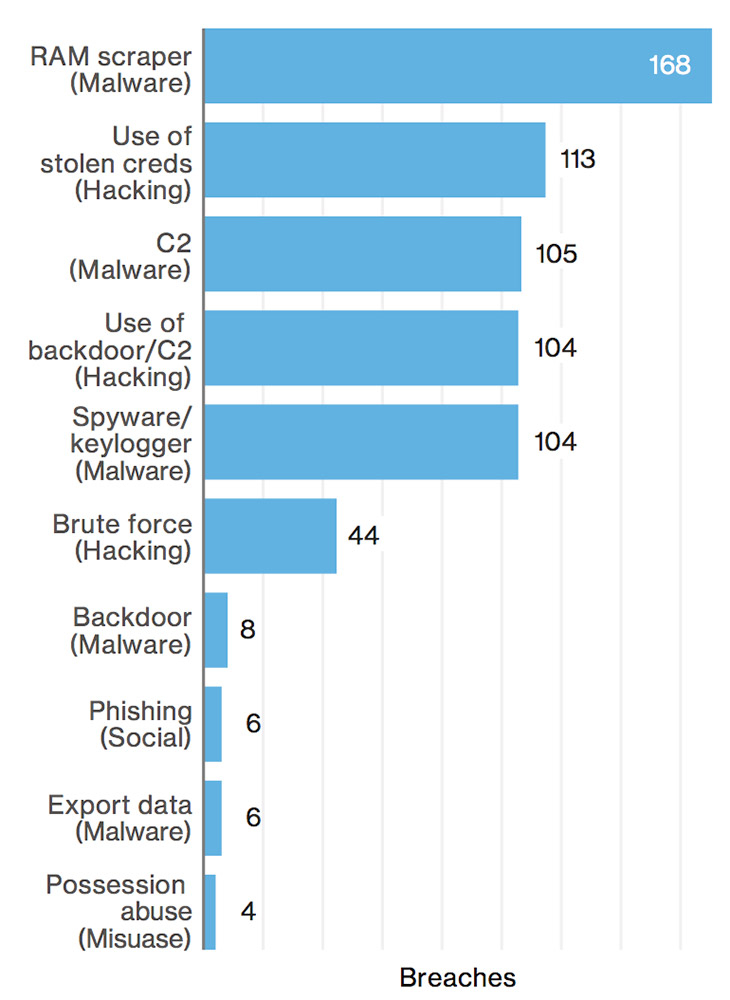
"While hotels likely come to mind first, restaurants also fall into this industry and comprise the majority of the victim population," the report reads. "Often food service victims are smaller businesses without IT departments, [or] CISOs ... but they do accept payment cards and are therefore a target for opportunistic attack."
Hospitality sector hackers have a clear goal: 96 percent of all breaches in the sector involved payment card data, with the majority of the compromised data being traced to breaches involving "third-party managed POS devices," including both terminals and controllers, according to the report.
Verizon suggests that too many hospitality organizations and providers are failing to put basic information security defenses in place, including banning default passwords on devices, filtering remote access to POS networks, patching and updating POS terminals and servers, as well as monitoring POS device integrity to help spot malware outbreaks.
Breaches may persist for months before being spotted, Verizon's report finds. "Breach timelines continue to paint a rather dismal picture - with time-to-compromise being only seconds, time-to-exfiltration taking days, and times to discovery and containment staying firmly in the months camp."
Few breached hospitality firms spot breaches on their own. Of nearly 200 recent cases counted in Verizon's report, 85 percent of the breaches came to light only once related fraud was spotted. Another 4 percent of the breaches, meanwhile, were first spotted by law enforcement agencies.














