ATM / POS Fraud , Cybercrime , Endpoint Security
Smooth 'Opera1er': French-Speaking Gang Steals $11 Million
Banks in Africa are Primary Targets, With Funds Getting Dispersed Using Money Mules
A French-speaking gang has been tied to the theft of at least $11 million, mainly from banks in Africa.
See Also: Cybercrime-as-a-Service: The High Cost of Digital Transformation on Fraud
The criminal syndicate, codenamed "Opera1er," remains "active and dangerous," according to a new report from cybersecurity firm Group-IB and the CERT Coordination Center at French multinational telecommunications giant Orange.
"Researchers codenamed the gang Opera1er after an email account frequently used by the gang to register their domains," Group-IB reports, adding that the gang is also known as Desktop-Group and NXSMS, while the Society for Worldwide Interbank Financial Telecommunication - aka SWIFT - in 2020 dubbed it Common Raven.
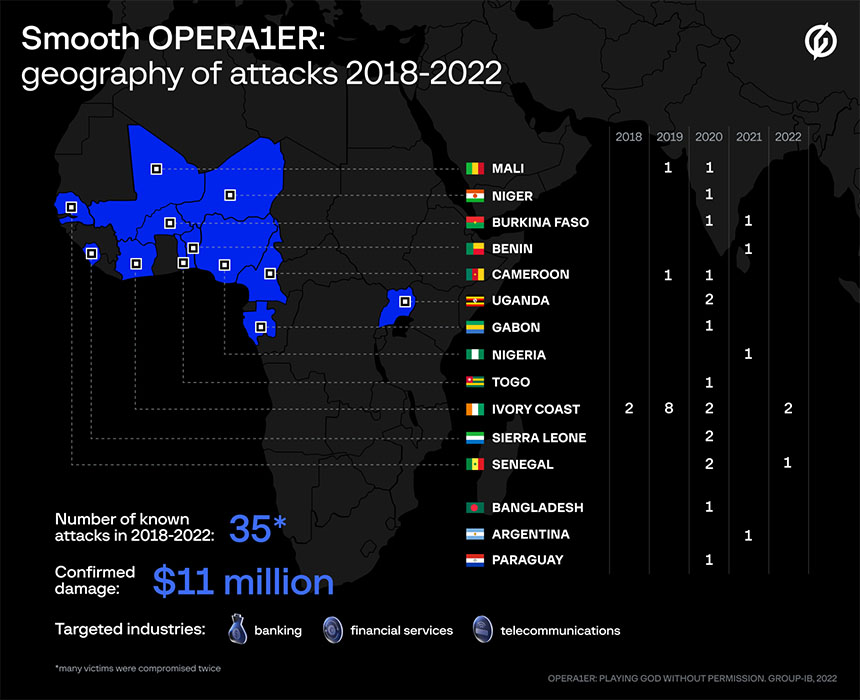
"Between 2018 and 2022, the gang managed to steal at least $11 million, and the actual amount of damage could be as high as $30 million," Group-IB reports. Victims have included financial services firms and telecommunications companies in Argentina, Bangladesh, Burkina Faso, Cameroon, Gabon, Ivory Coast, Mali, Niger, Nigeria, Paraguay, Senegal, Sierra Leone, Togo and Uganda. Researchers say the group prefers to hit victims on weekends or during public holidays.
Group-IB and Orange CERT-CC are releasing their findings, including TTPs and indicators of compromise, to help organizations - and especially banks - better spot attacks tied to this group. They say a number of other security researchers have helped track the group, including Polish cyber threat intelligence expert Przemysław Skowron, as well as researchers in Belgium, France and Switzerland, and Russian hosting provider Internet Hosting Center.
They report that plans to detail the group's activities last year were put on hold, after the attackers appeared to spot that they were being tracked and immediately deleted a number of accounts and altered their tactics, techniques and procedures.
"When this happened, we risked losing sight of them," says Rustam Mirkasymov, head of cyber threat research for Group-IB in Europe, in a blog post. "To avoid being outfoxed, the Group-IB team postponed publishing our findings until they revealed themselves again."
In the interim, the gang hit at least five more targets, including banks in Burkina Faso and Benin last year, followed by two banks in Ivory Coast and one in Senegal this year.
The gang's activities were first spotted in 2019, when Orange CERT-CC "detected a massive phishing campaign targeting banks and financial organizations in Africa and was asked to help manage a number of IT security incidents for an organization in Africa, which reported suspicious banking transactions during a weekend," according to the report. "During the investigation, security analysts quickly confirmed abnormal transactions that led to money being withdrawn from ATM machines. The analysts linked this attack with the same actor, which was responsible for the phishing campaign and reconstructed the incident timeline."
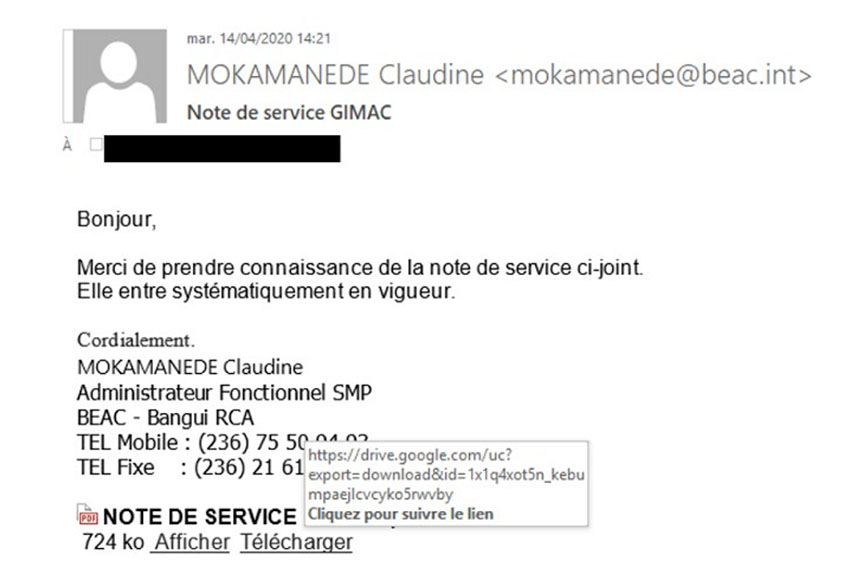
After gaining access to a victim's network, researchers say attackers will dwell in the network anywhere from three to 12 months before fraudulently withdrawing funds from ATMs. Attackers appear to have nothing unique in their attack arsenal, but rather use freely available tools, including open source software and software distributed via underground cybercrime forums.
The gang appears to be exclusively run by individuals for whom French is their primary language. "Their English is quite poor and so is their Russian," according to the report.
Researchers say the group often cashes out its attacks using money mules to withdraw cash from fraudulent accounts created by attackers, via ATMs. In one attack, it says a "vast network of 400 mule accounts for fraudulent money withdrawals" was used (see: Don't Be a Money Mule for the Holidays).
Group-IB says the gang was first identified in part because of its use of Cobalt Strike red-team software, including it deploying Cobalt Strike beacons and setting them to listen on port 777. While Cobalt Strike is commercial software marketed as "software for adversary simulations and red team operations," attackers regularly use cracked copies to distribute Cobalt Strike beacons - a payload that gets installed on a system - to infect PCs and build botnets that they can control from a command-and-control server (see: Block This Now: Cobalt Strike and Other Red-Team Tools).
Other TTPs used by the gang that researchers says banks should beware include use of BitRAT, a remote access Trojan designed to evade security defenses; deploying their own VPN infrastructure, such as off-the-shelf FrootVPN, to hide their infrastructure; and using free dynamic DNS services such as DynDNS, oftentimes in conjunction with mobile internet IP address ranges in Ivory Coast.
In some attacks, the gang successfully gained access to SWIFT software - apparently the Alliance Access application - being used by a bank. "In one incident, the hackers obtained access to an SMS server which could be used to bypass anti-fraud or to cash out money via payment systems or mobile banking systems," the report says. "In another incident, Opera1er used an antivirus update server which was deployed in the infrastructure as a pivoting point."
Researchers say it's not clear if attackers used their access to SWIFT software to steal funds, although it is possible. In some cases, they also appeared to have stolen funds after gaining direct access to a bank's payment systems.